Dashboard
System Security Update: Threat Monitoring and Management
System security updates help users monitor real-time security status, including the latest alerts and known threats across categories like Endpoint, Executable Files, Anti-Virus, and Extensions.
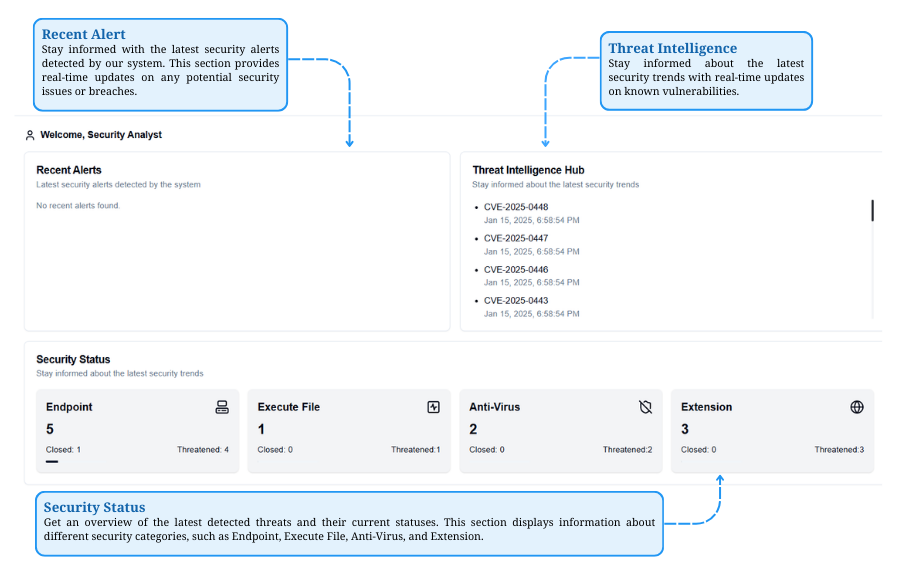
Explore The Platform
Endpoint (Phishing)
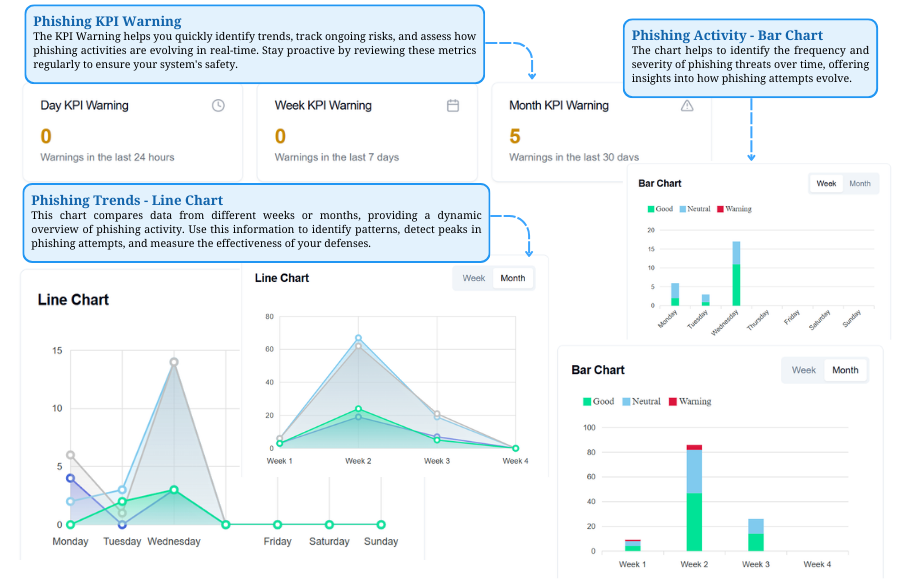
Phishing Dashboard
Monitoring Phishing Risks in Real-Time
The Phishing KPI Warning tracks risks, while bar and line charts show threat frequency, severity, and trends over time.
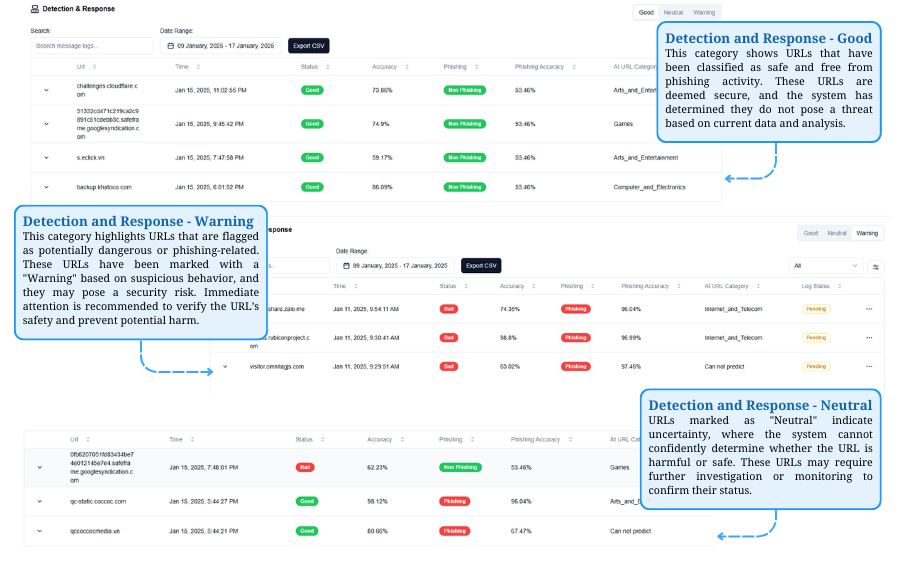
Phishing Detection & Response
URL Classification for Security Monitoring
The Good category marks safe URLs, the Warning category flags potentially dangerous ones, and the Neutral category indicates uncertainty, requiring further review.
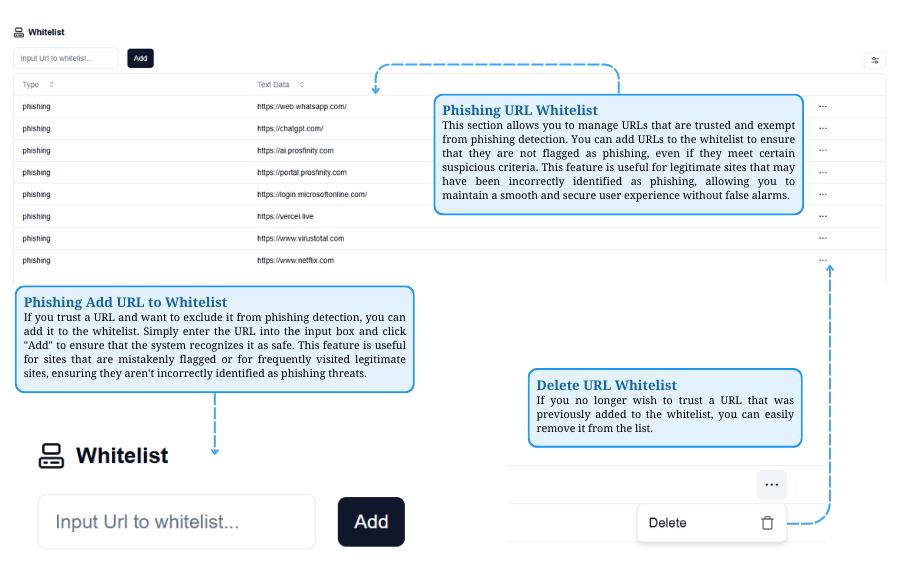
Phishing Whitelist
Managing Trusted URLs
The Whitelist allows trusted URLs to bypass phishing detection. You can add URLs to prevent false flags or remove them if they’re no longer trusted.
Execute File
Execute File Dashboard
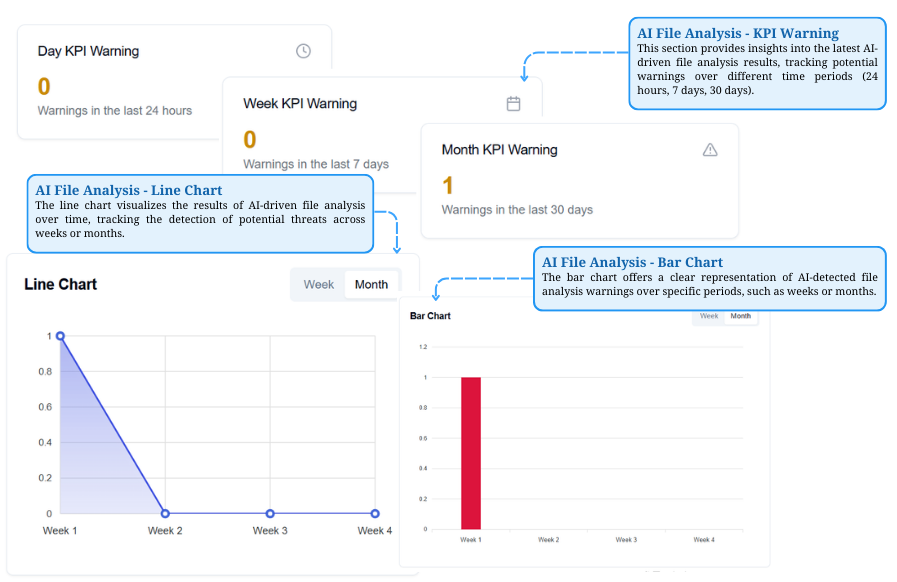
AI File Analysis Insights
Tracks AI-driven file analysis warnings with a KPI Warning, while line and bar charts visualize threat detection trends over time.
Execute File Detection & Response
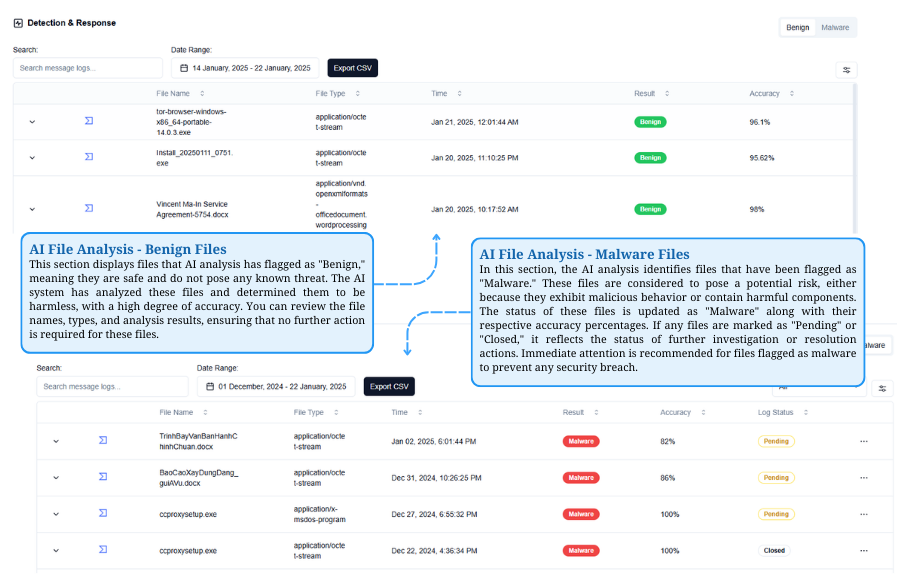
AI File Analysis Classification
Benign Files are safe and require no action, while Malware Files pose risks and need immediate attention to prevent security threats.
Execute File Whitelist
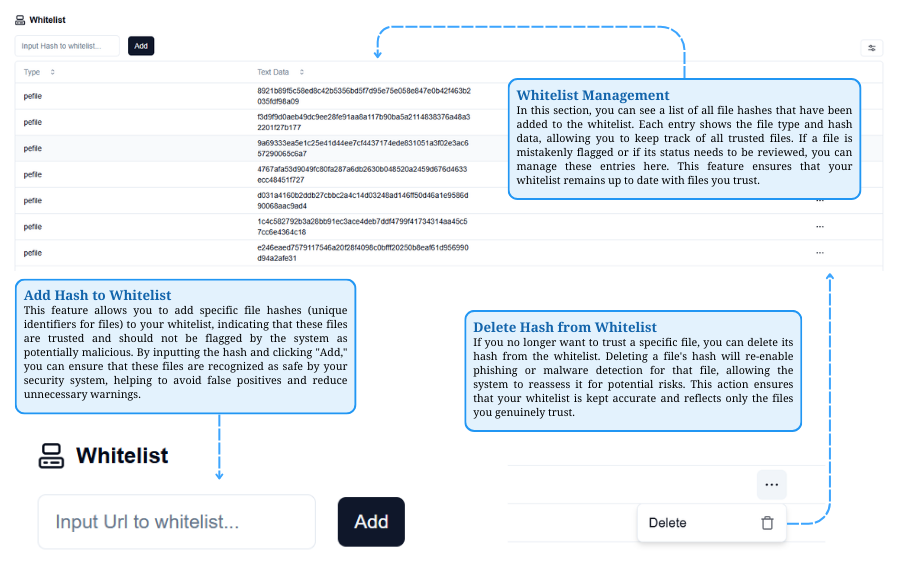
Managing Whitelisted Files
View and manage trusted file hashes in the Whitelist, add hashes to prevent false flags, or remove them to restore security checks.
Anti-Virus
Anti-Virus Dashboard
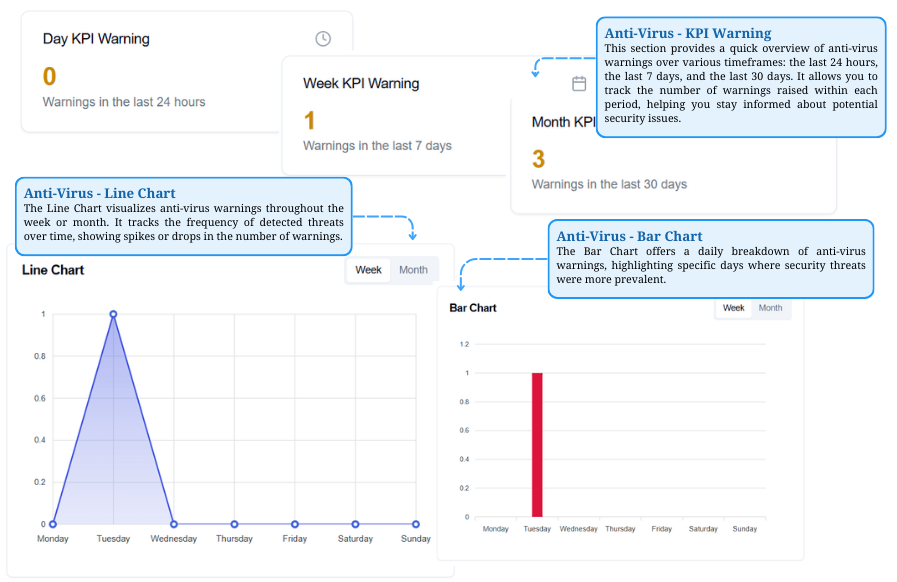
Anti-Virus Threat Monitoring
Tracks KPI warnings over time, with a line chart showing trends and a bar chart highlighting daily threat spikes.
Anti-Virus Detection & Response
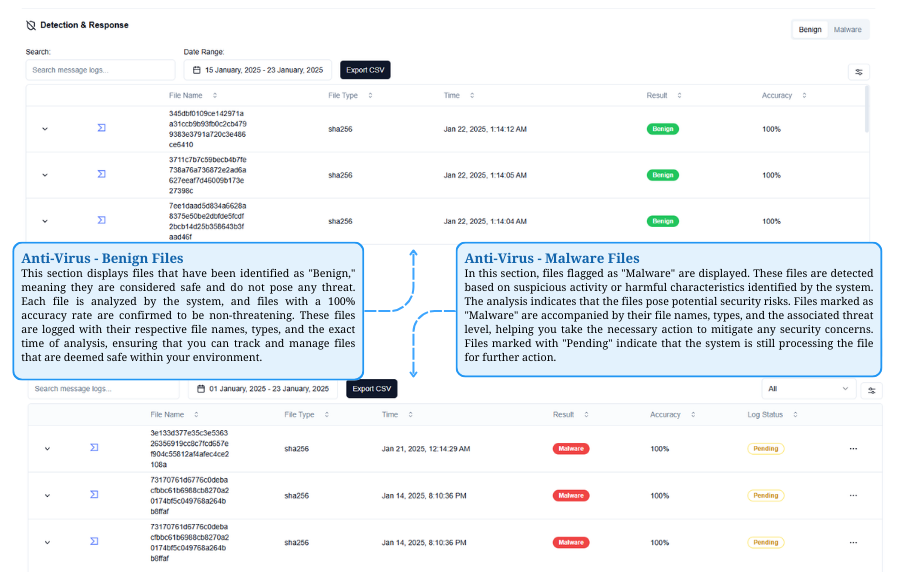
Anti-Virus File Classification
Benign Files are confirmed safe, while Malware Files pose security risks and require action based on threat analysis.
Anti-Virus Whitelist
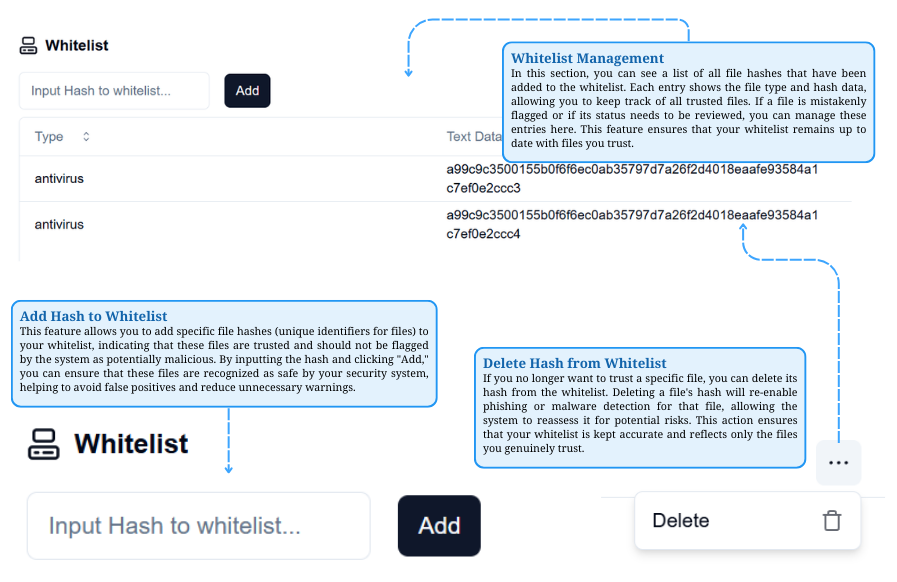
Whitelist Management
View and manage trusted file hashes, add hashes to prevent false flags, or remove them to restore security checks.
Global Settings
Users Management
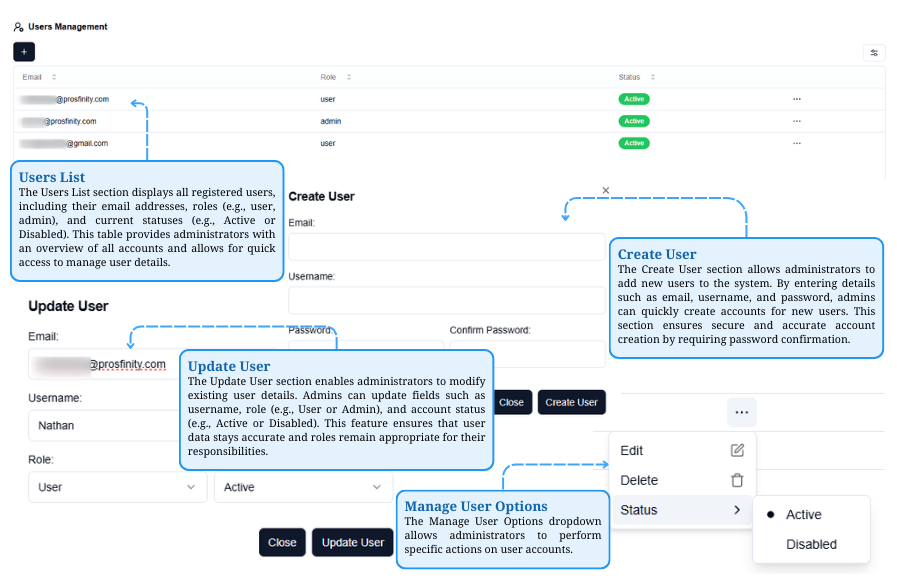
User Management Overview
The User Management section lets admins view, create, and update user accounts, including their roles and statuses. It also offers options to manage accounts through a dropdown menu.
Agents Status
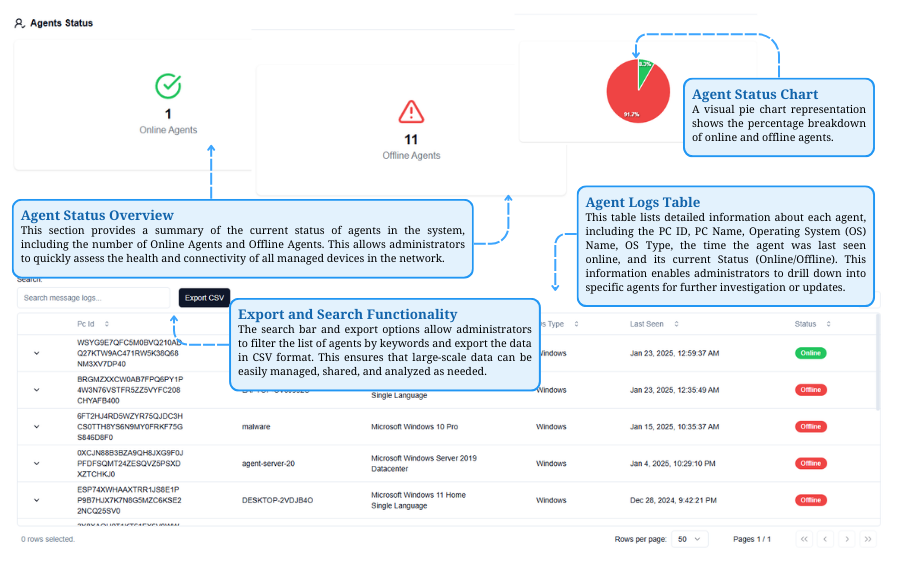
Agent Status Overview and Management
The Agent Status Overview section provides a summary of agent connectivity. It includes search and export options for managing data, a detailed agent log table with key information, and a visual pie chart showing agent status breakdown.
Policy
AI File Policy
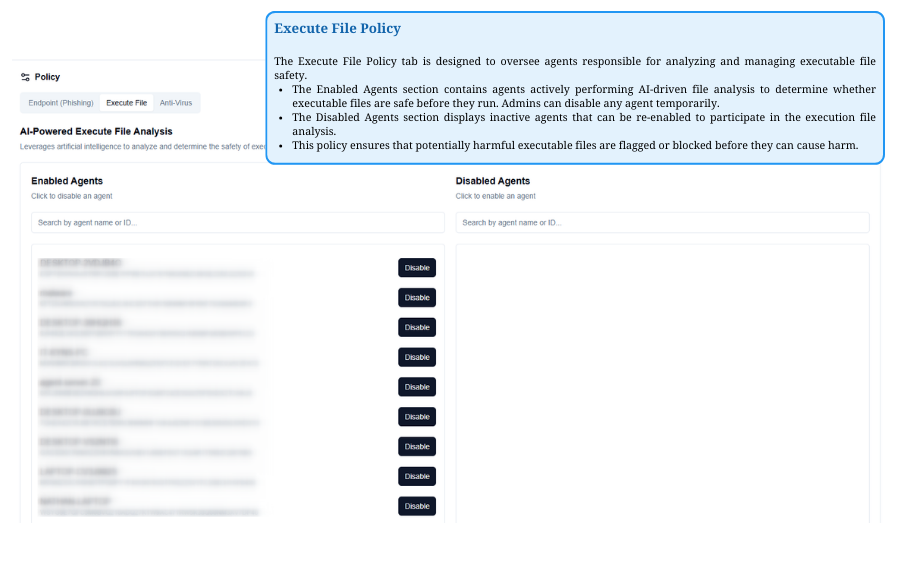
Execute File Policy
Manage agents analyzing executable file safety. Enabled Agents actively assess files, while Disabled Agents can be reactivated. This policy helps flag or block potential threats.
Anti-Virus Policy
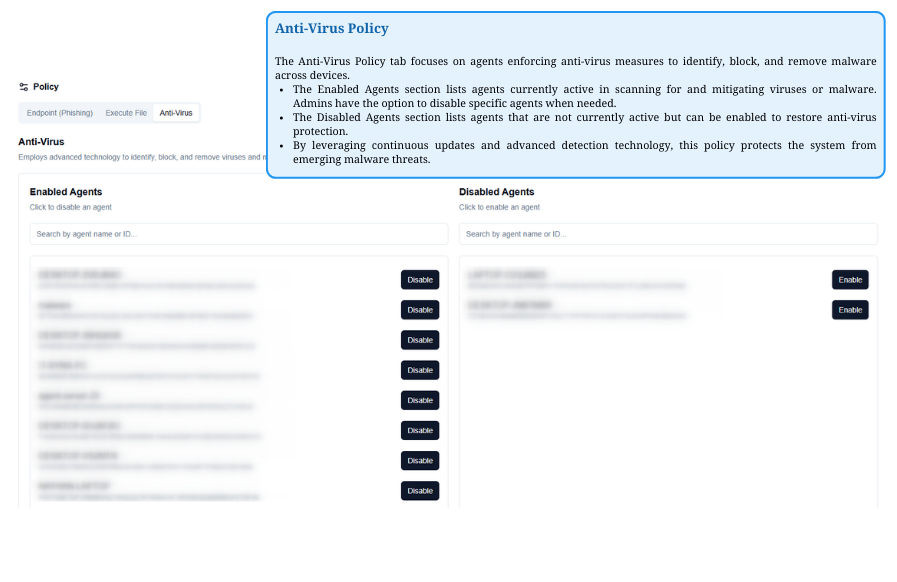
Anti-Virus Policy
Manage agents enforcing anti-virus protection. Enabled Agentsactively scan and remove threats, while Disabled Agents can be reactivated. This policy ensures continuous defense against evolving malware.
Phishing Policy
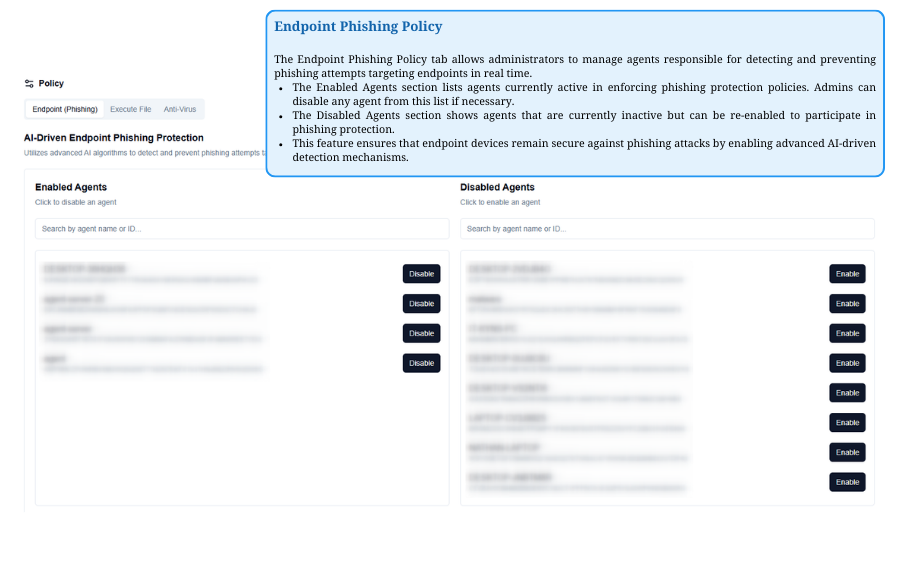
Endpoint Phishing Policy
Manage agents preventing phishing on endpoints. Enable or disable protection as needed to enhance security.
Settings
Setting
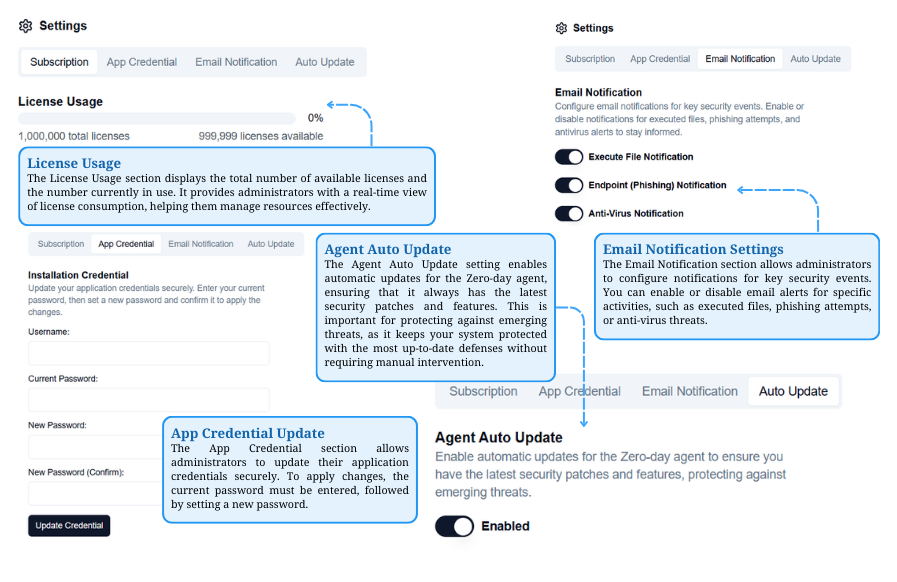
License & Security Settings
Tracks licenses, auto-updates agents, configures alerts, and secures credential updates.
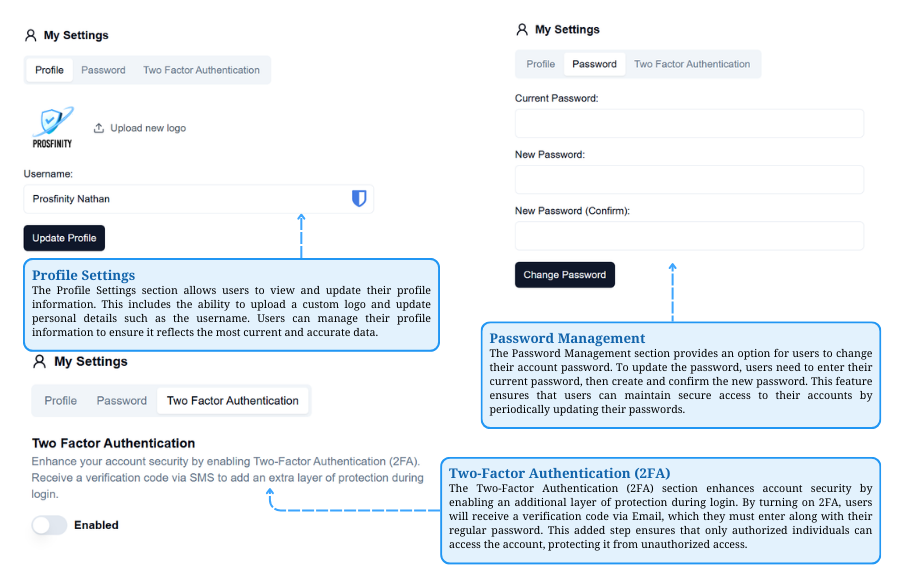
My Setting
Profile Management & Security Settings
Manage profile details, update passwords, and enable 2FA for enhanced security.
